New York’s Stop Hacks And Improve Electronic Data Security (SHIELD) Act

New York State is the latest addition to the rapid flurry of privacy, data protection, and cybersecurity regulatory frameworks proliferating on the international, national, and state levels.
On July 25, 2019, New York’s governor signed into law the SHIELD (Stop Hacks and Improve Electronic Data Security) Act. The Act amends New York’s current data breach statute by expanding the kinds of information deemed to be private and therefore protected and imposes new security measures for guarding such protected information. Further, the Act implements a more stringent breach notification regime and enhances enforcement authority. Like the CCPA and GDPR, the SHIELD Act has a broad jurisdictional reach and a multitude of compliance implications for a wide assortment of businesses.
The Kinds Of Information Regulated
Each privacy or data protection framework designates a term of art to encapsulate and define the categories of data regulated. For example, under HIPAA, it is PHI (Protected Health Information), whereas it is PII under the GDPR regime (Personally Identifiable Information). The SHIELD Act expands the assortment of personal data regulated under previous law and uses the technical term “private information” to refer to the kind of information regulated.
The SHIELD Act defines “personal information” as:
“any information concerning a natural person which, because of name, number, personal mark or other identifier, can be used to identify such a natural person.”
An area of confusion and an essential point of differentiation to stress is that, under the Act, “personal information” alone is not deemed to be regulated and hence protected “private information.” Instead, “personal information,” in combination with other specifically prescribed data points listed below, constitutes protected “private information.” We find it helpful to refer to this as the “personal information plus” framework. With that said, there is one instance under the Act where the presence of “personal information plus” is not necessary, and that is in a scenario where information allowing for access to an online account is accessed.
Protected “private information” includes the following:
- A user name or e-mail address in combination with a password or security question and answer that would permit access to an online account. As mentioned, there is no need for additional personal information for this category of information to be deemed “private information” and therefore protected.
- “Personal information” in combination with any of the following data elements is considered protected “private information”:
- social security number;
- driver’s license number or non-driver identification card number;
- account number, credit or debit card number, in combination with any required security code, access code, or password or other information that would permit access to an individual’s financial account;
- account number, credit or debit card number, where such numbers could be used to access an individual’s financial account without additional identifying information such as with a security code or password;
- biometric information, particularly data generated by electronic measurements of an individual’s unique physical characteristics, such as a fingerprint, voice print, retina or iris image, or other unique physical or digital representation of biometric data used to authenticate or ascertain an individual’s identity.
Triggers Of The Act
The Act is triggered when there is a “breach of the security of the system.” A breach now includes even just unauthorized access, whereas the previous law that the Act amends required some acquisition of protected information for notification to be required. Though there is now a lower threshold for what constitutes a breach and hence notification, there is still room for discretionary analysis under the Act for determining whether there was the requisite “unauthorized access.” In making this determination, an entity “…may consider, among other factors, indications that the information was viewed, communicated with, used, or altered by a person without valid authorization.” Still, as can be seen from the Act’s wording, there are many instances where even a potentially benign instance of “unauthorized access” will result in a need for notification.
Notification Obligations
Under the Act, businesses must notify affected New York residents that their private information was accessed without authorization due to a breach. Notice of the breach must also be communicated with the New York Attorney General.
Security Requirements
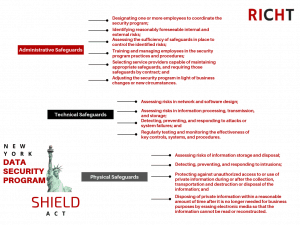
Aside from the amendments that the SHIELD Act institutes regarding the kind of information regulated and the definition of “breach,” there is a significant addition that relates to security measures that businesses must undertake to safeguard private information. The Act states that businesses who collect the private information of New York residents must:
“develop, implement and maintain reasonable safeguards to protect the security, confidentiality, and integrity of the private information.”
As per the Act, the standard relating to security measures is one of “reasonableness.” Exactly what suffices as “reasonable safeguards” varies widely depending on the specific business sector and associated risk profile. With that said, the Act does prescribe specific measures to meet the reasonableness standard in terms of overall security that includes a mix of policies, procedures, and technical safeguards.
We have listed the outlined security measures in the adjacent chart.
The requirement for security measures is similar to the existing security controls imposed on financial institutions by the New York Department of Financial Services (DFS). Taking inspiration from DFS, proper implementation of security protocols under the Act involves employee training, risk assessment, incident response, and a vendor vetting and management process. Compliance with the security provisions of HIPAA, GLBA, and DFS-regulated entities is recognized as meeting the security components of the SHIELD Act.
When it comes to the security requirements, the Act lightens the compliance load for small businesses. A small business is deemed to comply with the data security requirement if reasonable safeguards are implemented, even without performing the specific steps outlined in the Act. In the words of the Act, safeguards should be “appropriate for the size and complexity of the small business, the nature, and scope of the small business’s activities, and the sensitivity of the personal information the small business collects from or about consumers.” 1
Entities Covered Under The Act
The SHIELD Act applies to any person or business that owns or licenses computerized data that includes private information of New York residents. The Act significantly expands upon the range of entities subject to New York’s data breach notification law. Whereas previously, only businesses that conducted business in New York were regulated, now the law applies where a person or business “owns or licenses computerized data which includes private information of any resident of New York.”
Enforcement Of The Act
In a scenario where data breach notification violations are not reckless or knowing, the court may award damages for actual costs or losses incurred by a person entitled to notice. For knowing and reckless violations, the court may impose a penalty the greater of either $5,000 or $20 per instance of failure to notify, not to exceed $250,000.
If a business obligated to comply with the reasonable security measures fails to do so, the New York Attorney General may prosecute such noncompliance as an unfair business practice and may seek an injunction.
The Act excludes the private right of action.
Effective Dates
The Act takes effect starting on October 23, 2019, except the security component. The security requirements mandated by the Act take effect on March 21, 2020.
The New York Attorney General Is Ramping Up Enforcement
New York’s Attorney General is continuing to bring enforcement actions against businesses experiencing breaches that are deemed to have had inadequate data security or for not complying with breach notification timelines.
The latest complaint, filed in September 2019, is against Dunkin’ Brands, Inc., the franchisor of Dunkin Donuts. The complaint alleges that by failing to sufficiently guard customer information and notify them of a breach that occurred, Dunkin’ Brands violated both its promises to consumers as well as obligations under New York Law. The cause of actions included in the complaint is a variety of consumer protection laws relating to deceptive practices and false advertising, as well as breach notification statutes.
The lawsuit against Dunkin’ comes hot on the heels of a recent settlement by NY’s AG with Bombas, a popular direct-to-consumer sock start-up. That case involved an investigation that found the company failed to employ timely notification customers of a data breach, which affected nearly 40,000 accounts. The complaint asserted that by failing to inform these consumers and relevant New York authorities “in an expedient time-period, and without unreasonable delay,” Bombas violated New York’s breach notification statute, which is General Business Law Section 899-AA. The terms of the settlement included $65,000 in penalties and implementing improvements to both technical and physical security to safeguard customer data.
These two actions were before the effective dates of the SHIELD Act. As discussed previously in this discussion, the Act has instituted more stringent requirements relating to data security and breach notification. We can, therefore, expect to see more enforcement actions as well as the potential for more severe penalties.
Going Forward
In preparing for compliance with the SHIELD Act, businesses should form a breach response plan and implement notification procedures for consumers and all relevant regulators. Knowing what kinds of information is under inventory and keeping track of it on a granular level is necessary. Further, businesses should ensure that their security and associated procedures align with the reasonableness standard used in the Act. Implementing the prescribed security components included in the Act should be the starting point. Generally, maintaining data security best practices relevant to a business’s specific sector is necessary.